搜索结果: 1-15 共查到“Break-Up”相关记录112条 . 查询时间(0.046 秒)
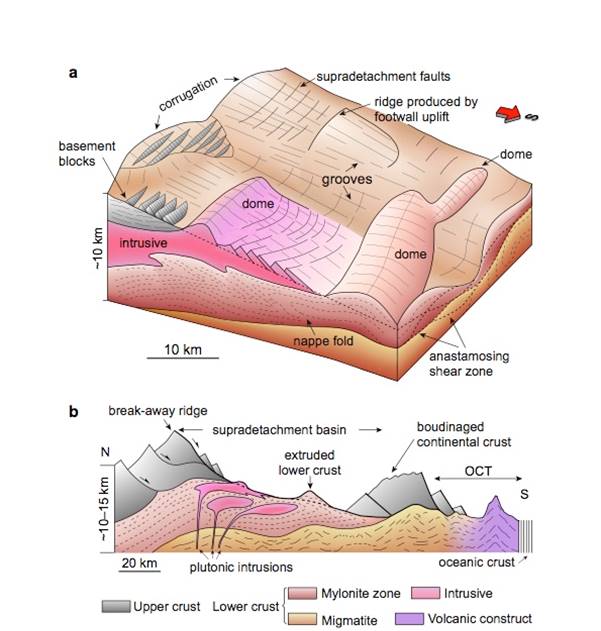
中国地质大学科学技术发展院邓洪旦*,任建业 等,海洋学院. Nature Communications(2020), South China Sea documents the transition from wide continental rift to continental break up(图)
三维;高清;地震数据;南海北部;被动陆缘大型;拆离;断层
2021/10/15
近日,中国地质大学海洋学院邓洪旦博士和任建业教授在国际著名科学期刊《Nature Communications》发表题为“South China Sea documents the transition from wide continental rift to continental break up”的学术论文。
How to not break SIDH
isogenies SIDH cryptanalysis
2019/5/27
We give a number of approaches which, to a newcomer, may seem like natural ways to attack the SIDH/SIKE protocol, and explain why each of these approaches seems to fail, at least with the specific set...
Attacks Only Get Better: How to Break FF3 on Large Domains
Format-preserving encryption attacks
2019/3/2
We improve the attack of Durak and Vaudenay (CRYPTO'17) on NIST Format-Preserving Encryption standard FF3, reducing the running time from O(N5)O(N5) to O(N17/6)O(N17/6) for domain ZN×ZNZN×ZN. Concrete...
Deniable messaging protocols allow two parties to have `off-the-record' conversations without leaving any record that can convince external verifiers about what either of them said during the conversa...
SPATIO-TEMPORAL PROCESS SIMULATION OF DAM-BREAK FLOOD BASED ON SPH
Smooth Particle Hydrodynamics GIS Dam-break Flood Spatio-temporal Process Simulation
2018/5/15
On the basis of introducing the SPH (Smooth Particle Hydrodynamics) simulation method, the key research problems were given solutions in this paper, which ere the spatial scale and temporal scale adap...
How to Break Secure Boot on FPGA SoCs through Malicious Hardware
FPGA SoCs secure boot hardware design
2017/6/28
Embedded IoT devices are often built upon large system on chip computing platforms running a significant stack of software. For certain computation-intensive operations such as signal processing or en...
Total Break of the Fully Homomorphic Multivariate Encryption Scheme of 2017/458: Decryption can not be of low degree
Multivariate Cryptography Fully Homomorphic Encryption Eprint 2017/458
2017/5/31
Total Break of the Fully Homomorphic Multivariate Encryption Scheme of 2017/458: Decryption can not be of low degree.
Determining the Nonexistent Terms of Non-linear Multivariate Polynomials: How to Break Grain-128 More Efficiently
Stream ciphers Grain-128 Polynomial reduction
2017/5/15
In this paper, we propose a reduction technique that can be used to determine the density of IV terms of a complex multivariable boolean polynomial. Using this technique, we revisit the dynamic cube a...
Evaluation of dormancy break in some selected peach (Prunus persica) cultivars
Prunus persica (L.) Batsch endogenous dormancy length of dormancy flower buds
2016/12/8
The evaluation of dormancy break based on the number of flower buds in bloom was performed in years 2011–2013 (January–April) for 15 peach cultivars compared to the control cv. Redhaven. Based on the ...
Total Break of Zorro using Linear and Differential Attacks
Zorro Differential Attack Linear Attack
2016/1/25
An AES-like lightweight block cipher, namely Zorro, was proposed in CHES 2013. While it has a 16-byte state, it uses only 4 S-Boxes per round. This weak nonlinearity was widely criticized, insofar as ...
SIMON Says, Break the Area Records for Symmetric Key Block Ciphers on FPGAs
Block Ciphers Light-Weight Cryptography
2016/1/23
While AES is extensively in use in a number of applications, its area cost limits its deployment in resource constrained platforms. In this paper, we have implemented SIMON, a recent promising low-c...
Automatic break-line detection from laserscanner data using surface flatness
Spatial Information Sciences Automation Cultural Heritage Extraction
2015/8/25
Recently, a laser scanner has been receiving more attention as a useful tool for real-time 3D data acquisition, and various applications such as city modelling, DTM generation and 3D modelling of cult...
3D MODELING OF STRUCTURES USING BREAK-LINES AND CORNERS IN 3D POINT CLOWD DATA
Cultural Heritage Modeling Visualization Laser scanning Representation
2015/8/7
Recently, a laser scanner has been receiving more attention as a useful tool for real-time 3D data
acquisition, and various applications such as city modeling, DTM generation and 3D modeling of cult...
Stress Fracture of the Ulna in a Break-Dancer
Sports injuries ulna fractures stress fractures magnetic resonance imaging
2015/4/17
Break dancing is a popular activity in teenagers and is associated with severe trauma to bones and tissues. We report the first known case of a break dancer with an ulnar stress fracture. Such injurie...
Cut and break verbs in Ewe and the causative alternation construction
cut and break separation events verb semantics
2015/3/30
Ewe verbs covering the cutting and breaking domain divide into four morpho-syntactic classes that can be ranked according to agentivity. We demonstrate that the highly non-agentive break verbs partici...

